Home » KeyFortress™ Workstation » Features
Encryption and Decryption Software

For thousands of years, humankind and its diverse cultures, from the Egyptians to the Hebrews, have worked to perfect the encryption of information and communications to limit the reach and understanding of confidential information to authorized individuals.
This principle continues to be applied years later to businesses, who today are vulnerable to information theft attacks that could harm trade secrets, intellectual property and especially the commercial and financial information management of their operations.
How do encryption and decryption work?
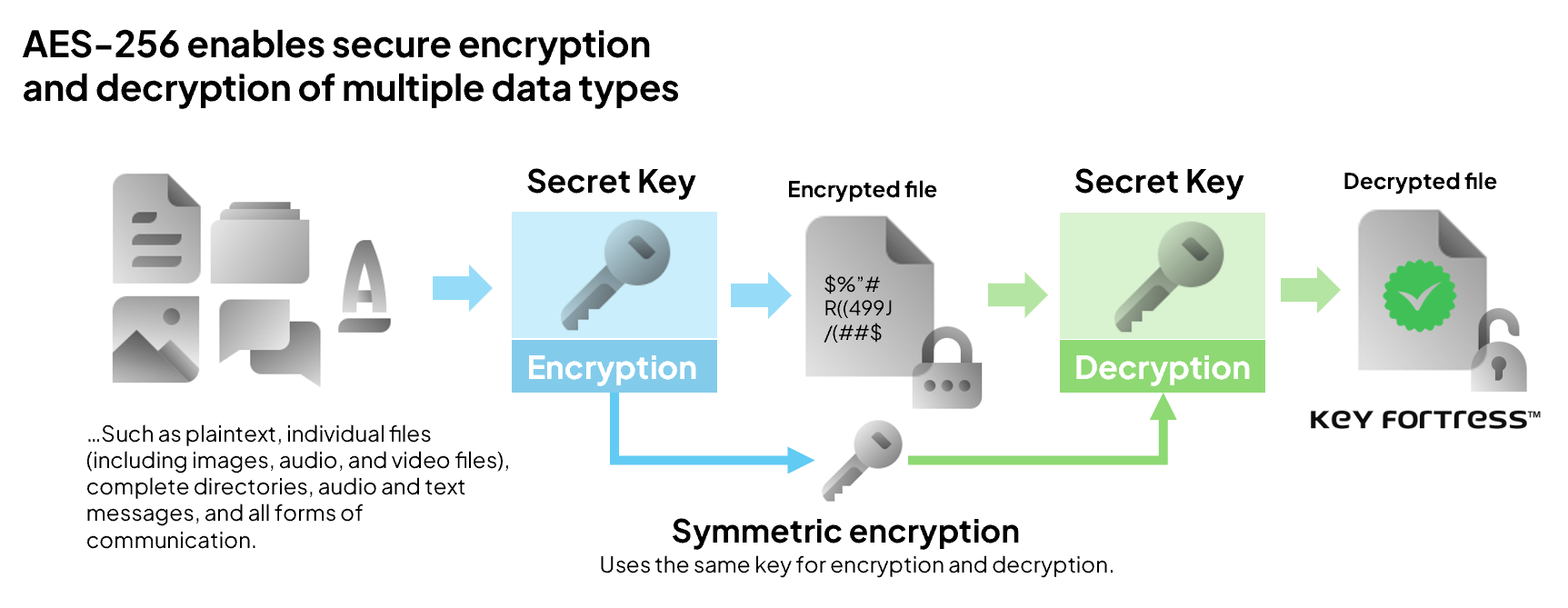
AES-256 encryption is currently the most widely used and accessible method for protecting and encrypting information, files, conversations, and databases with a single password. This type of encryption is known as symmetric encryption because the same password used for encryption is also used for decryption.
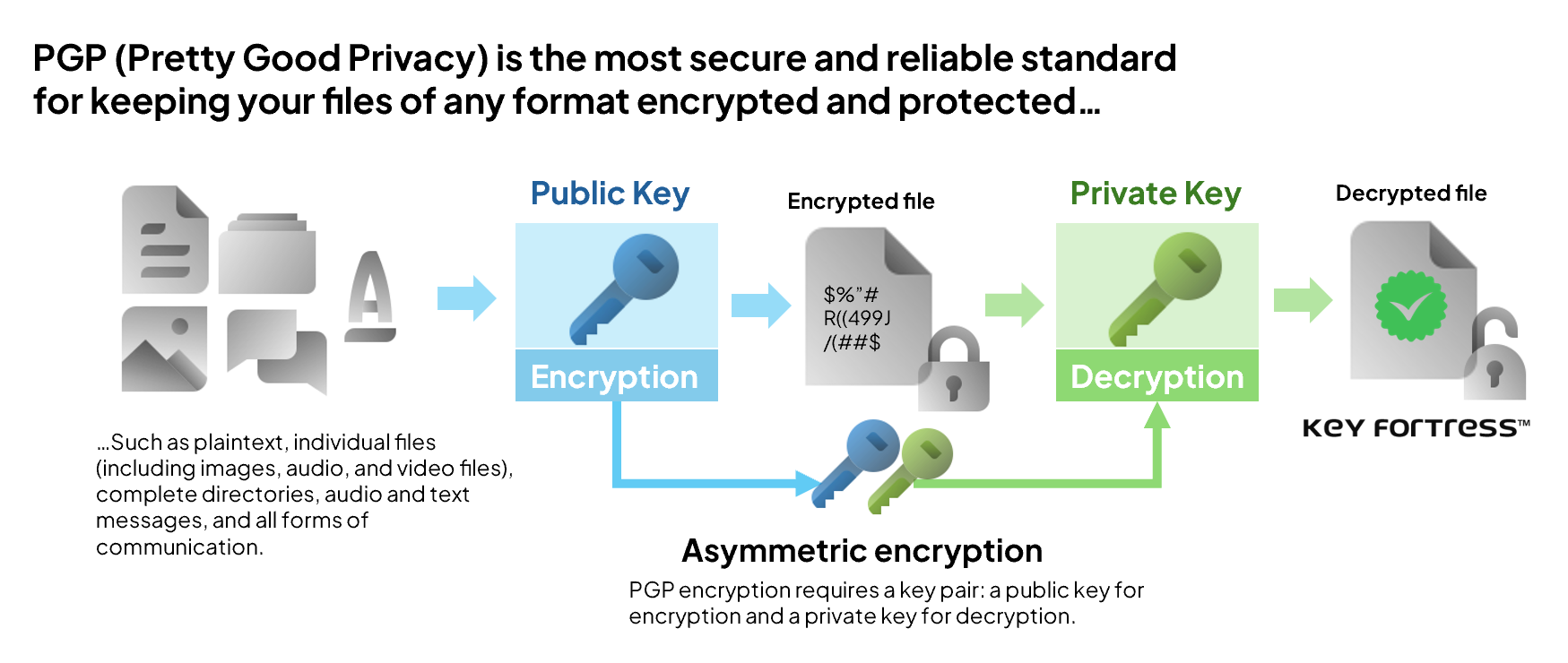
The PGP encryption standard uses two separate keys: one for encryption (the public key) and one for decryption (the private key), asymmetric encryption. This standard is ideal for host-to-host banking and encrypting files at rest. PGP is KeyFortress‘s primary encryption standard.
What standards are used to encrypt and decrypt files?
These standards provide different levels of security, key lengths, and performance characteristics for encrypting and decrypting files across various platforms and use cases.
Symmetric Encryption Standards:
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- 3DES (Triple DES)
- Blowfish
- Twofish
Asymmetric Encryption Standards:
- RSA
- ECC (Elliptic Curve Cryptography)
- Diffie-Hellman key exchange
Hybrid Encryption Standards:
- PGP (Pretty Good Privacy)
- GPG (GNU Privacy Guard)